Microsoft Loop is now in Public Preview!
We’ve been super excited about Microsoft Loop since it was first previewed at Ignite in March 2021. I may have possibly squealed with glee when Loop components first appeared in Teams in January 2022, and we quickly threw out a video on the YouTubes showing how easy a Loop is to use.
Things went a little quiet from the Loop…group(?)… for a while, but by the end of last year we started to see Loop integrations in Outlook. However, the dedicated app that was promised was still over the horizon.
Last week Microsoft sent Loop live, and it’s absolutely as neat as was promised, and will support the new Copilot capabilities that were also announced in March 2023, along with a new capability that eases the “getting started” challenge of looking at a blank page.
But the way it was sent live was something I hadn’t seen before. We’re very accustomed to Microsoft releasing new tools in “Public Preview”, and we’ve known for years that this status is typically reserved for solutions that don’t yet meet the full range of Microsoft’s compliance capabilities or requirements. Products in Public Preview, however, are fully supported. So running preview products doesn’t necessarily expose you to any additional security or supportability risks, but it may carry compliance risk.
So sure, fine: Loop doesn’t meet all the requirements, and the pre-release announcement in the Admin Center confirms this:

And yes, that probably means it’s a great idea to roll it out “default off”, but the steps to enable it are where we step into new territory.
When your users first navigate to https://loop.microsoft.com, they will see a page telling them that the whole organization don’t have access:
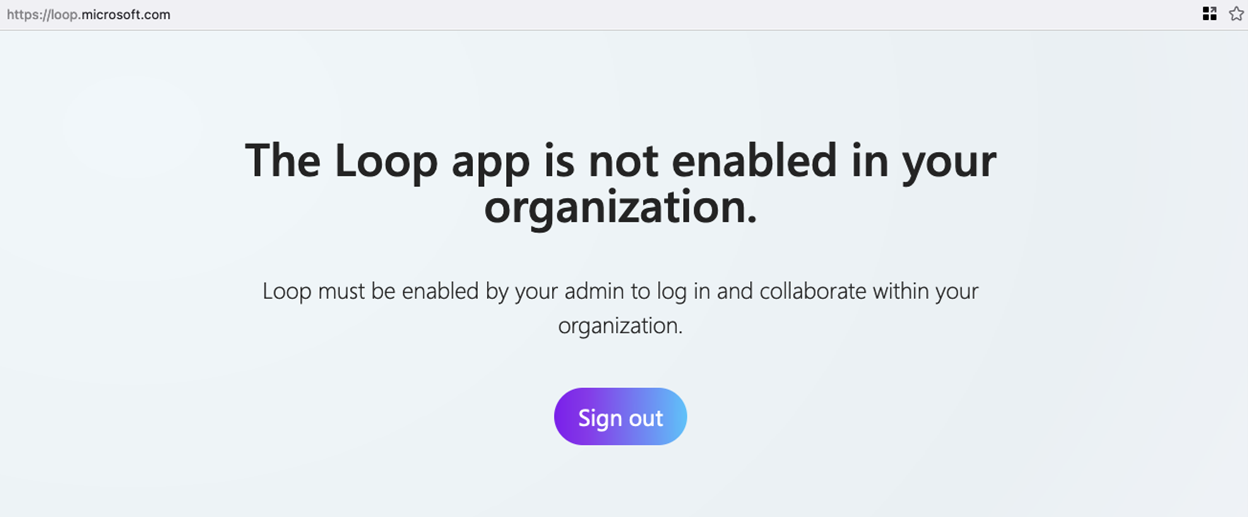
To go from that sad screen to this happy screen…
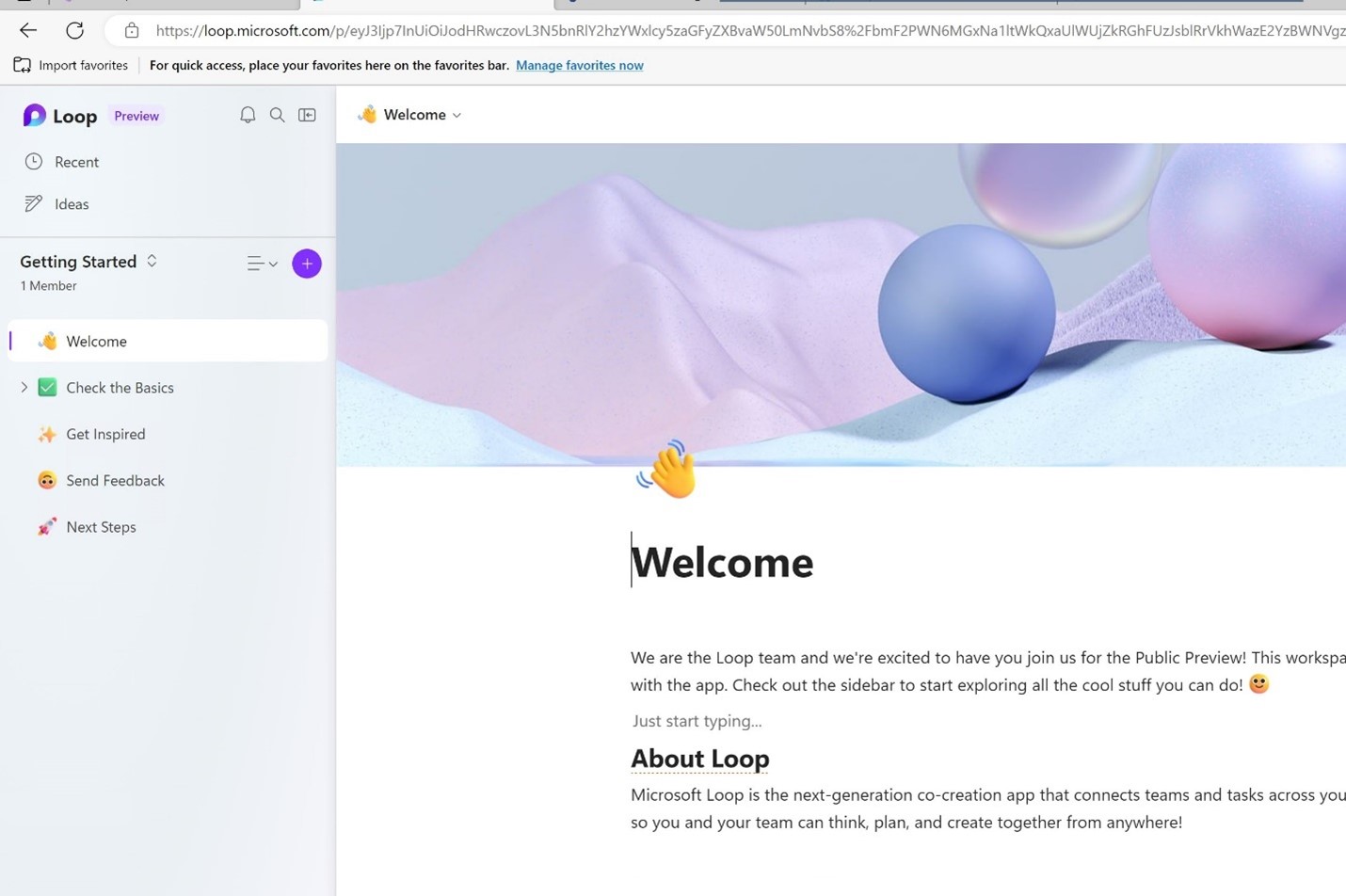
…you’re going to need to visit the least-touched administrative interface in the Microsoft cloud: the Office Policy Service.
If you’ve spent any time in the app configuration sections in Intune, you’ve probably seen Office policies:
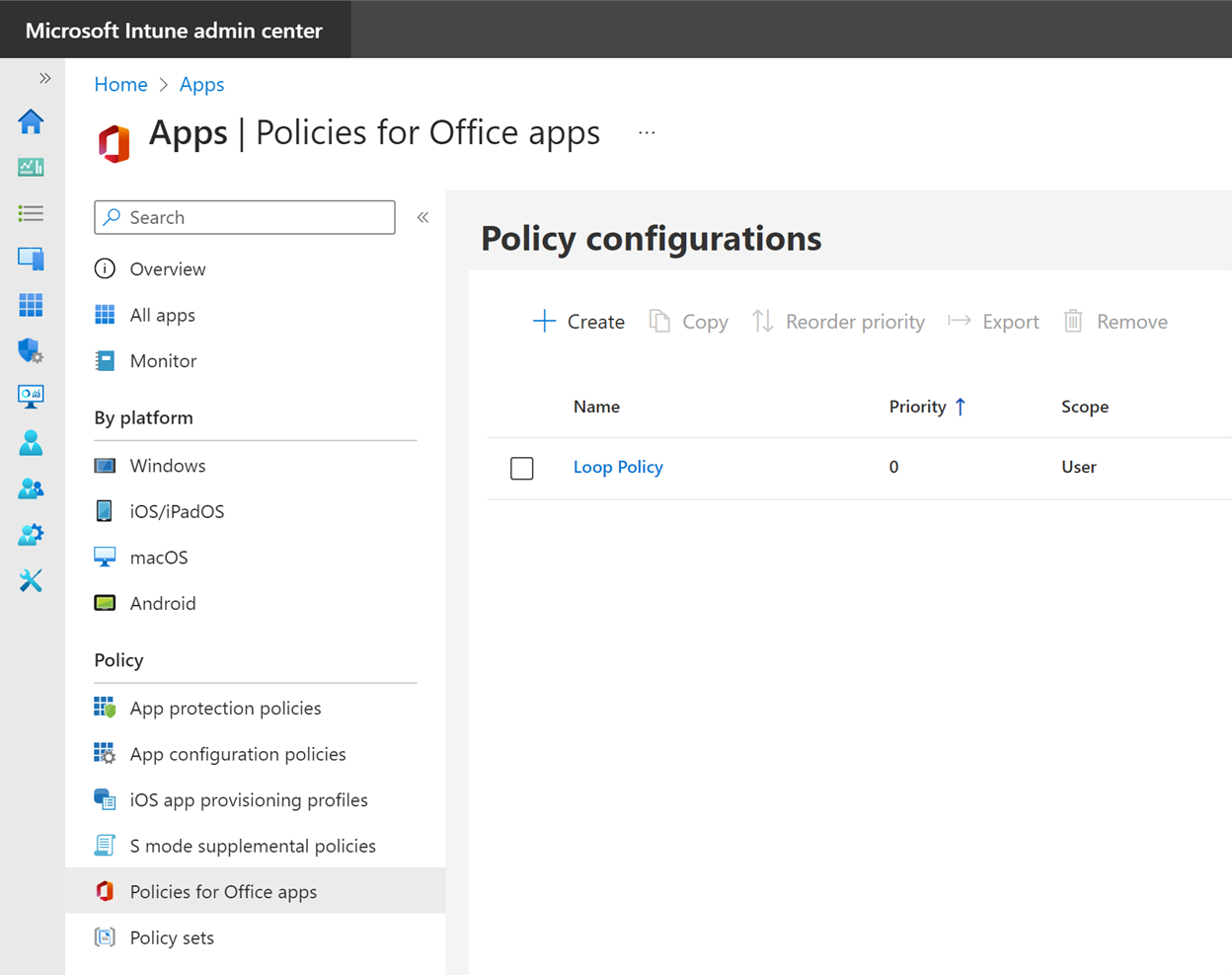
These give you the ability to control the experience of using Office/Microsoft365 apps at the tenant level. There is a lot of overlap between these settings and what can be managed from an Intune device configuration profile, but these are rather explicitly designed to manage the app experience, more so than the experience of running the app on a given device. But because there’s so much overlap, and probably because so many of us come from Group Policy/Configuration Manager backgrounds, we tend to stay in our device management lane. That’s groovy, too - you just can’t use that avenue to enable Loop.
But while you can absolutely create your Loop policy from inside the Intune portal’s App Policy blade, there’s a lot more to the Office Config Service than what’s surfaced here. To get the rest of the experience, we need to go to https://config.office.com, aka the “Microsoft 365 Apps Admin Center” (some documentation also refers to this as the “Office Configuration Tool”):
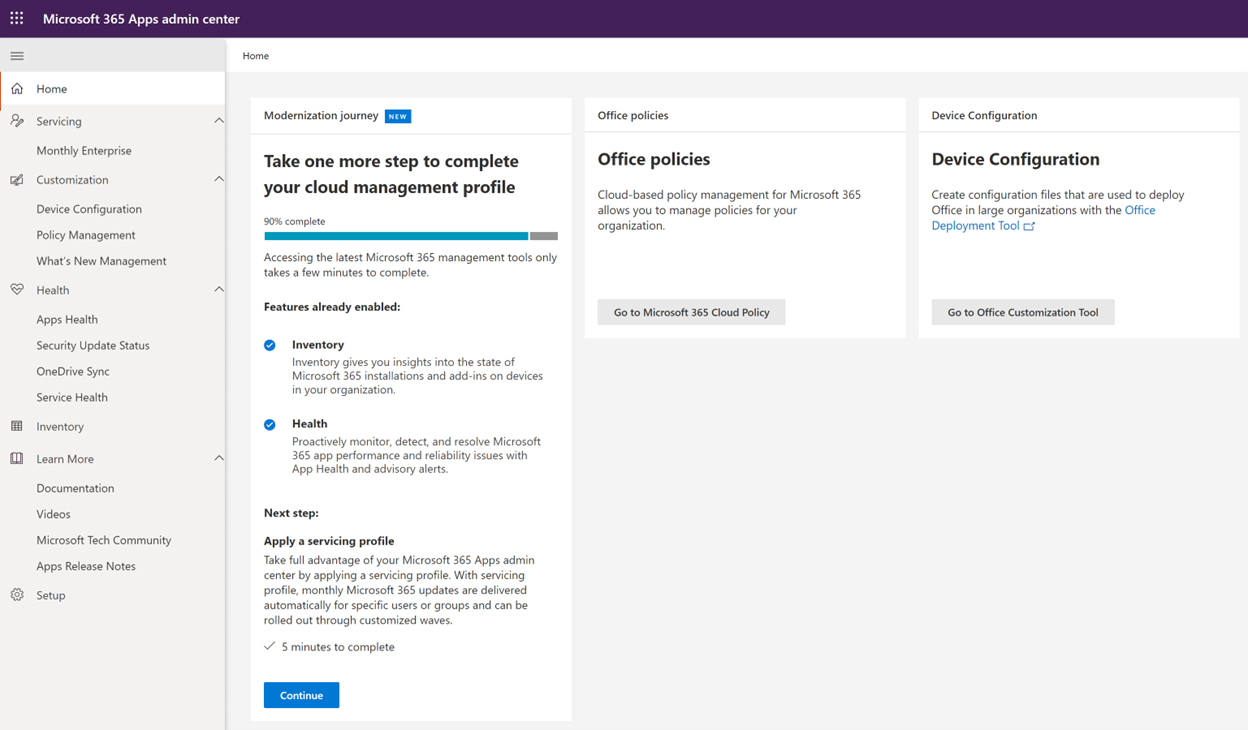
While there’s nothing more exciting than discovering a new dashboard, let’s address the gap it fills: public documentation for the M365 Apps Admin Center explicitly states that it’s intended for large deployments of the Office suite. How large?
Pretty large.
It’s not really necessary for configuring deployments in the SMB/SMC market, so if you’re not on an Enterprise Agreement, you’ve probably been safe to ignore this. And to be clear, even though the steps to enable Loop show this portal, you don’t actually have to do it here. You can stay safely within the confines of the Intune dashboard’s App configuration blade.
But since we’re here, let’s poke around! Since it’s our first time here, many of the blades may not be populated. Much like auditing in Microsoft 365, these are datasets you opt into, but there’s nothing better than free data, so turn on all the dials & switches and come back after a day or two.
In my absurdly tiny environment of 1 active user, the most interesting blade is the Inventory. Here we see a breakdown of the various active builds, servicing channels, processing architectures, and add-ins that have been detected on our devices.
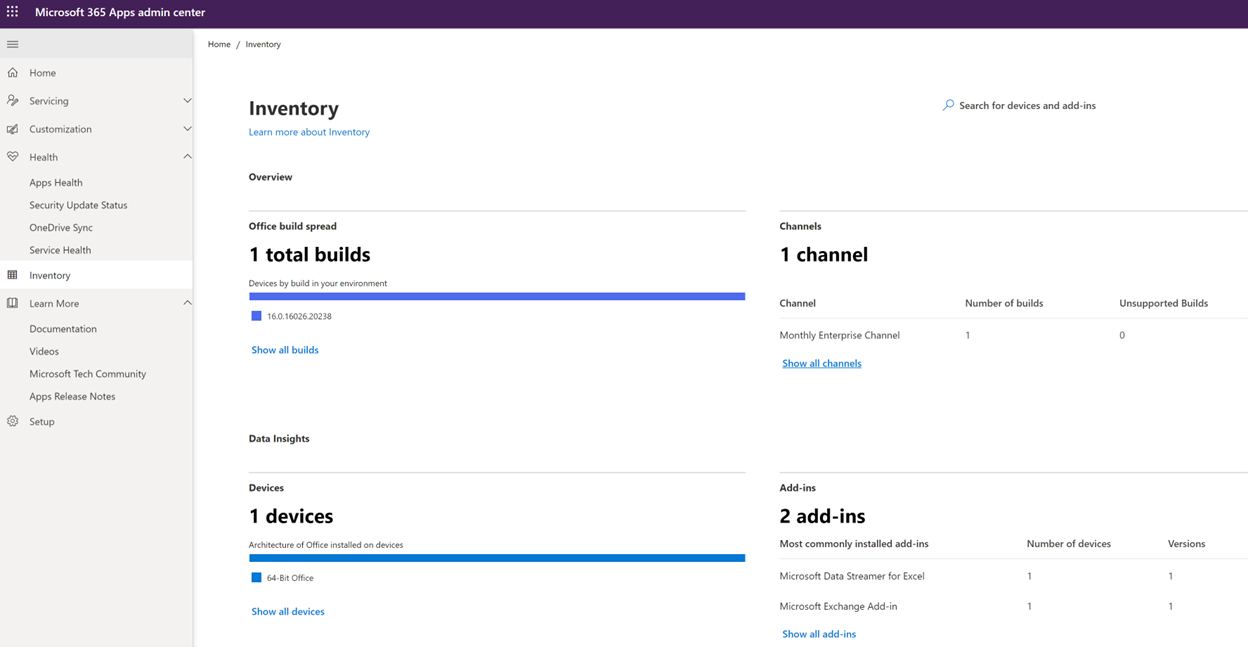
We’ve been seeing more and more application inventorying from both Intune and Microsoft Defender for Endpoint (MDE), but whereas MDE tells us builds and vulnerabilities and Intune just gives us versions, this fills in a lot of gaps that are important for organizations managing those afore-mentioned large deployments. Probably the most important detail is the add-ins, which can make or break an Office deployment:
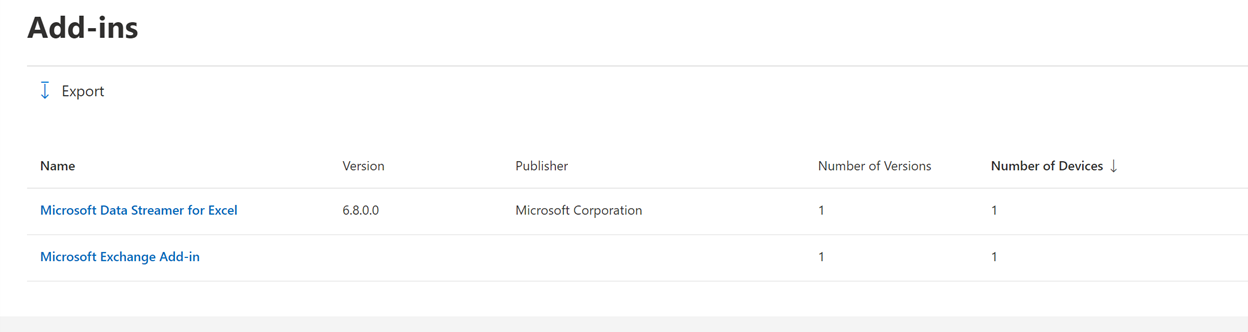
Clicking in to the “Microsoft Data Streamer for Excel” add-in, we can surface a lot more information about the devices that have it running:
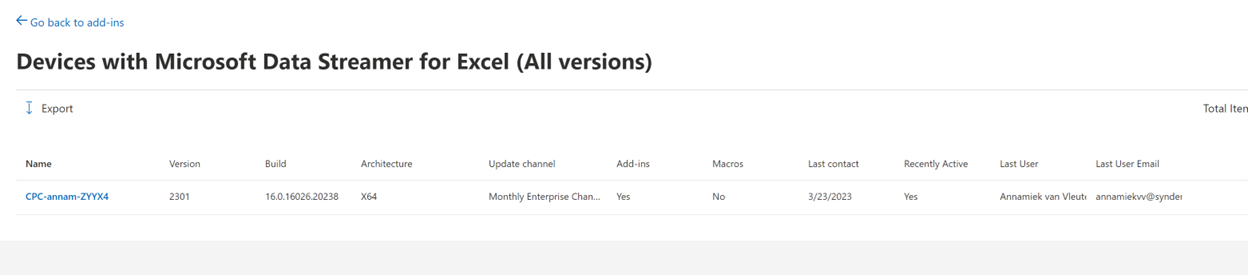
Now we know exactly whose desk to visit when we have an add-in blocking issue for a version upgrade!
But we also get a heap of information about our actual Office deployments, and even though I’ve only been using one device in the lab lately, fortunately the Apps Health blade detected some additional machines that have been largely dormant.
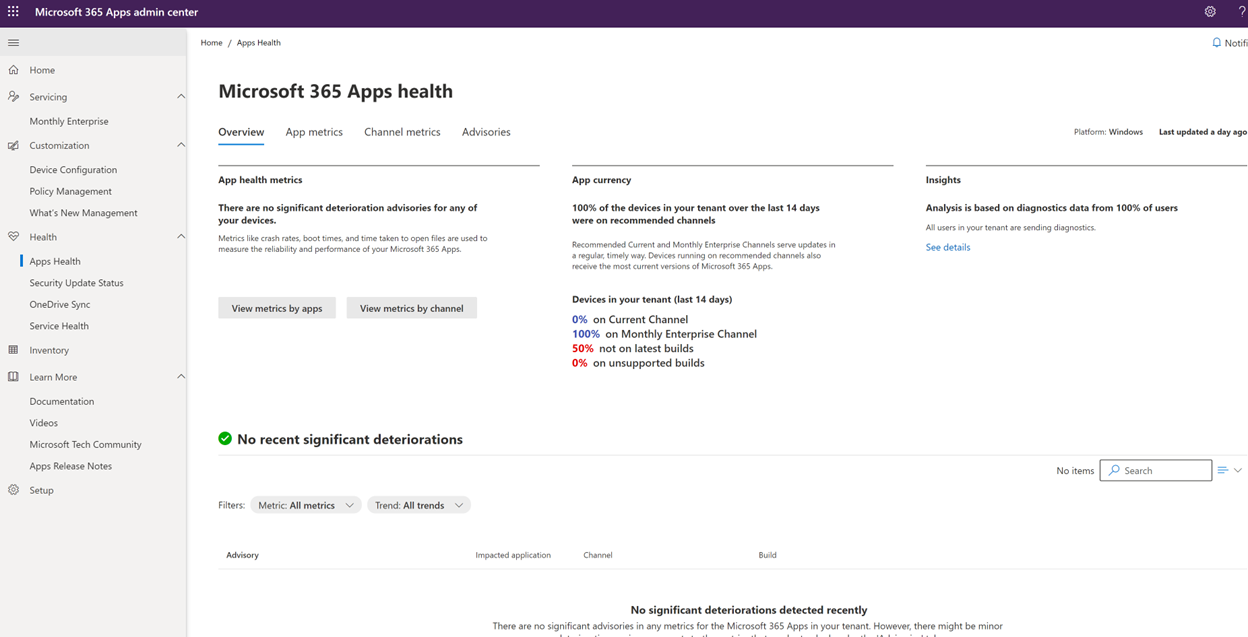
I can see here that while nothing appears to be broken, some of my devices are falling behind. I can chase that by moving to the Channel Metrics tab, where I see a breakdown of the builds in my environment, along with session data, per-app metrics across a range of measured stats, and support information like release and EoS dates.
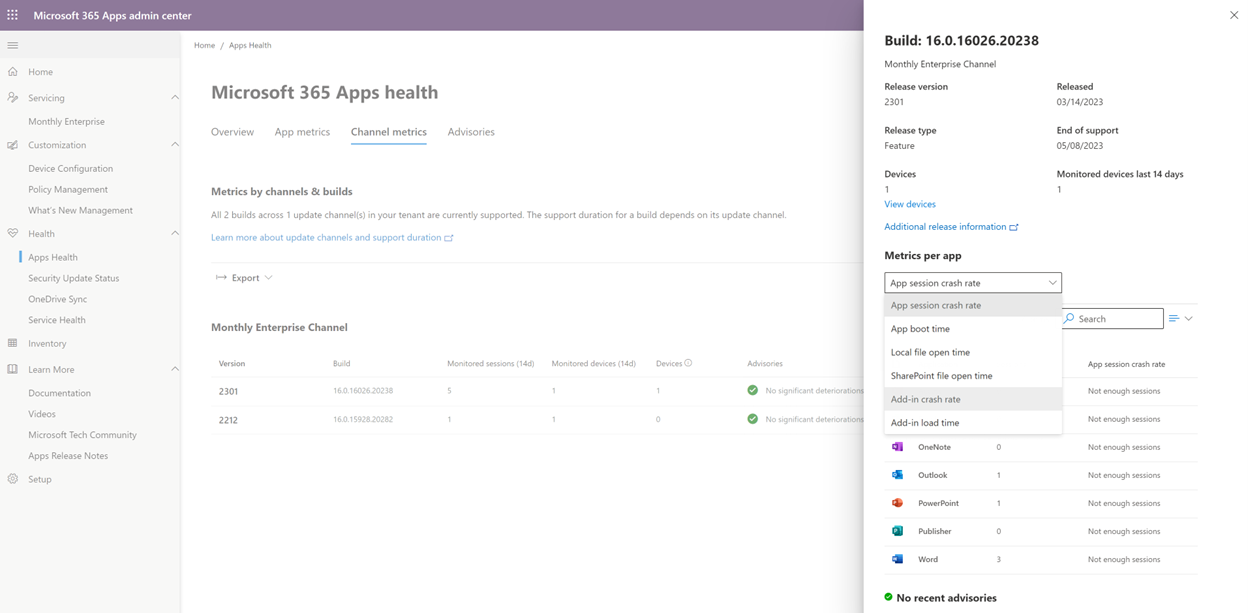
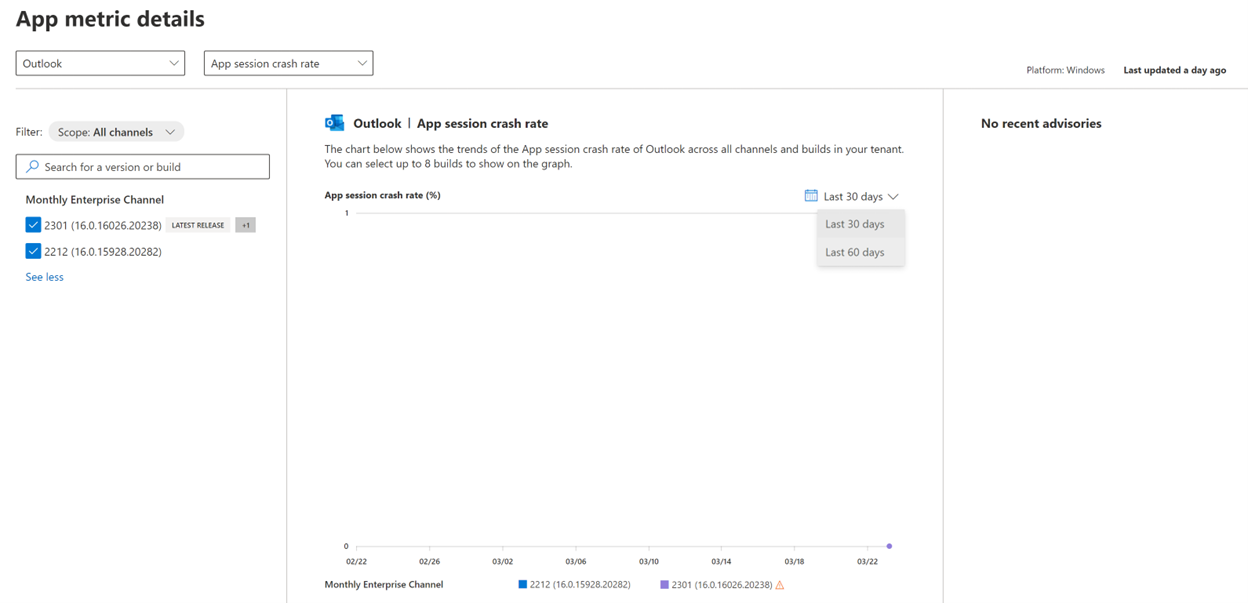
I can also click on any of the apps in that fly-out blade on the right and get even more details going back over the previous 30 or 60 days.
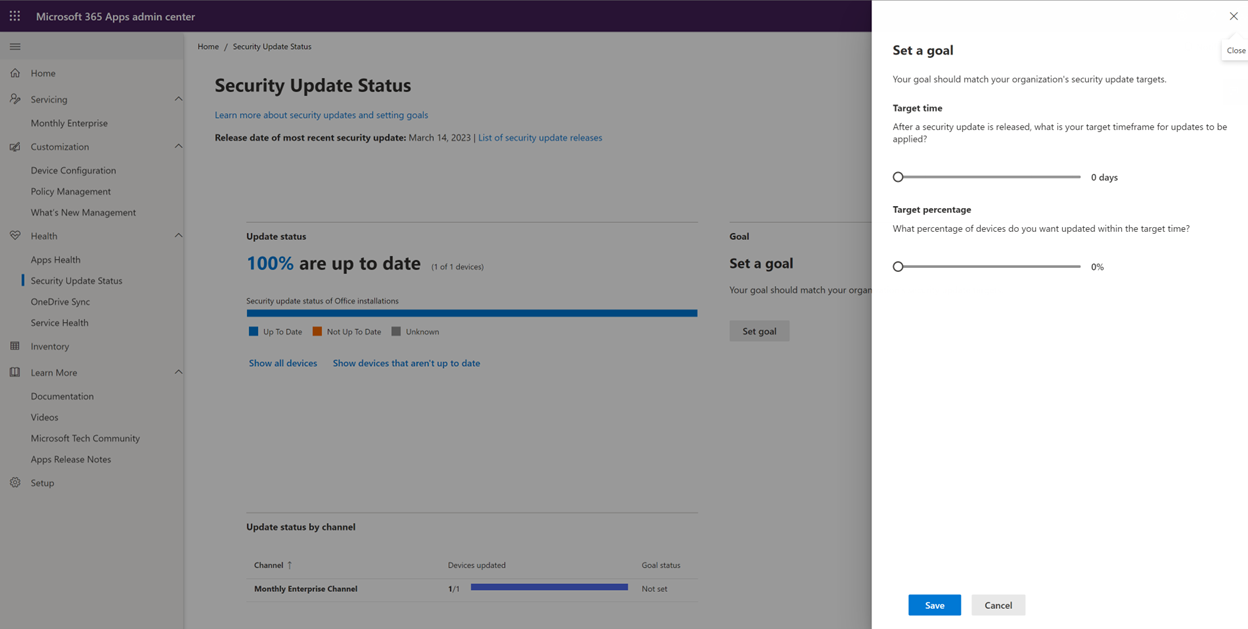
There’s also security update monitoring, with built-in goal tracking, and details across various servicing channels:
There’s also a whole blade just for OneDrive sync, which had no details by press-time.
All of this is fantastic data. It’s great to have visibility into version distribution without having to provide security console access to your apps deployment team, to be able to see application health, and to understand the application risk for your next upgrade. But unless you fall into the “large organization” category, I’m going to suggest you stop here. Because the rest of this toolset is potentially disruptive to your deployments. So much so, in fact, that I’m going to cover it in a separate post.
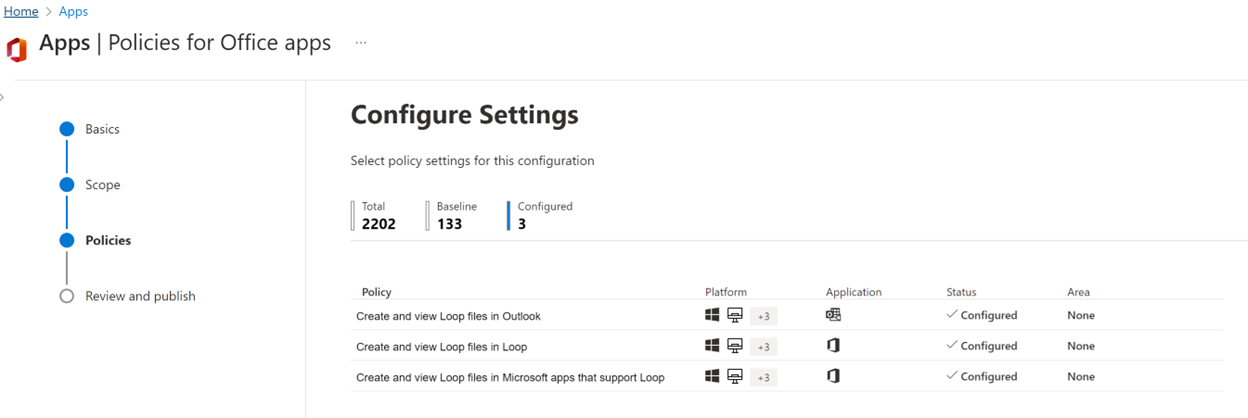
For now, cruise back over to the Intune Apps Policy blade, build your Loop Policy (only 3 settings!), and start enjoying the new Loop experience.
Would you like to find out more about Intune & Endpoint Manager? Learn how you can manage & protect your devices, apps, & users with Endpoint Manager.


Comments