Microsoft Weekly Round-up

Inspire was pretty awesome, and I have to thank Lexi Burroughs for handling the major coverage so I could focus on some of the other impactful announcements. If you missed anything you can always look in the Book of News! Obviously there's a lot of buzz around Windows 365, which I like to think Microsoft released entirely to validate my round-up post from last week, but the biggest question seems to be around the differences between it and Azure Virtual Desktop. Nerdio has a whole bunch of amazing content to help untangle the mess, but my take is that Microsoft has taken all the learnings of the past 2 years of AVD to work out the kinks and deliver a simplified experience. It's not the same, but it's not exactly intended to be the same, so if you're using AVD today, don't worry about having to start over. The one thing that won't be there when it goes live on August 2 is native Azure AD-only support for enterprise customers, so you'll have to go Hybrid Azure AD to be first on the bus, but that support is coming, and in fact will be there day-one for business customers. Ever thought, "man this live webinar I'm conducting is so cool, I wish I could expand my reach to say, the entire world"? RTMP streaming support is coming to Teams events. Blow up the Youtubes! Every time there's a new version of Windows people start assuming Microsoft will immediately drop support for the current version, so they were quick to announce that Windows 10 21H2 will happen. Also note the next LTSC version will be based on this upcoming release. Remember Kaseya and our social media posts about 68% of compromised companies being attacked again within 12 months? Follow-up exploits didn't take long. I guess maybe don't let users pick updates from "Jimmy's backyard update shack"? Managed devices should always only ever consume updates from Microsoft update. Set up your Intune Update Rings and delivery optimization profiles! Enable Defender for Endpoint and configure MDAC to only run signed trusted code, and tighten down those compliance & Conditional Access policies to ensure devices under attack do not have access to corporate resources. You can spend years trying to learn the ins & outs of Azure AD threat hunting, dig through thousands of circular-reference articles, and learn the minutiae of Kusto, or you can just go read Huy's article. It's amazing, instructive, illustrative, and THOROUGH. Not to be outdone, though, Microsoft followed suit with an Azure AD SecOps guide. Oh and that reminds me: PrintNightmare just keeps on keepin' on with a new vulnerability announced Friday night. Can we stop printing now? OAuth integrations enable fantastic interactions with apps, vendors, and all kinds of good stuff without standing admin access (yay!), but OAuth integrations aren't always trustworthy, and users rarely read through the publisher information before clicking the 'accept' button:
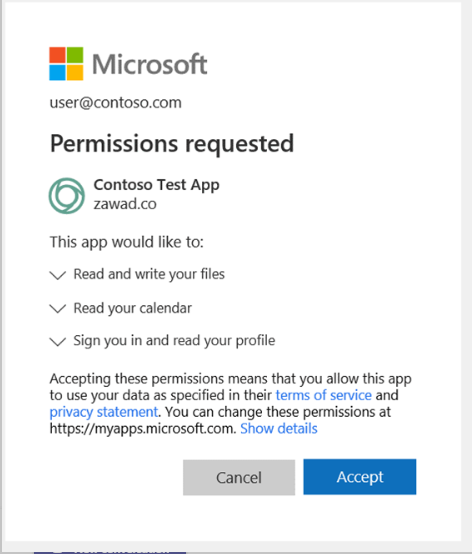
TBH I'd wager most admins don't read 'em, either. So you end up with a bunch of active consents for apps may have been tested and abandoned, and they operate as open doors into your environment. That's attractive to attackers, and there's been a steady rise in consent phishing. And there's a new tool to help fight both the phishing and the sprawl. In my mind this is the security announcement of the week. App Governance is in public preview and integrates into the Compliance Center, but is technically part of MCAS, which further reinforces my long-standing theory that MCAS will soon be fully integrated into the Security and Compliance dashboards. Oh and MCAS is GA in GCC. LMNOP.


Comments