The Future of Hybrid Work
On April 5th, Microsoft hosted a 90-minute event on Windows 11 and the future of hybrid work. For a 90-minute event, this was a big event. Like big enough that it answered the question of "why no Spring Ignite this year?" Big enough to get Panos and Satya to make special appearances.
What we got in that 90 minutes was the kind of roadmap data that sometimes takes 6 months to pull together, showcasing a lot of awesome new features and capabilities coming to Windows 11, Windows 365, Endpoint Manager, and productivity toolsets.
To be honest, it's kinda unfair to list those as separate entities, because as Satya said: "The boundaries between your PC and the cloud are fading away." Windows 11 is becoming more and more intertwined with Windows 365, with a new native app, the ability to treat the Windows 365 instance as if it were simply another desktop available within Windows, the super cool "boot to Windows 365" function, and future offline-mode support. Let's dig into each and examine what they are and what they mean for the future of hybrid work.
In Satya's address, he said the following about Windows 365: "And with Windows 365 we created a complete new category: the Cloud PC. Bringing the operating system to the cloud for the first time, so you can stream the full Windows experience to any device. You can think of it as a Windows computer with Azure computing." He talked about frontline workers, financial services, public sector, and even the remotest of the remote workers - areas we've traditionally seen steered towards other virtualization platforms.
We'll start with the new Windows 365 app, which will do away with the old "Remote Desktop" app (or should I say "apps," because there were 2: both had the exact same name and wildly different capabilities), and will come pre-installed on future versions of Windows 11 and will be available for Windows 10 users, as well.
The new app will bring together the features of both the old app and the web interface at windows365.microsoft.com, which so far had been the only place to initiate a restart, restore, resize, or reset. In fact the flow of the first-run experience of the new app looks an awful lot like the first-run experience in the current website, so it looks like the intent here is to tidy up the whole experience into a single native flow. Kudos to Microsoft for that, because it also looks like the app can ingest the integrated Windows logon experience to pass you directly to your environment, rather than having the user subscribe. The other thing that's nice here is that the Remote Desktop app "workspaces" are gone, so users simply see all of their available Cloud PCs in a single unified view.
This new experience looks like it's designed for a single user to access only their specific single-org Cloud PCs. No word yet on whether or not this new app will support connection to multiple users across multiple tenants.
What it will support, though, and I'm crazy excited about, is running Windows 365 as an additional desktop in your Task Switcher. When I'm presenting, I'll almost always drag all non-presentation windows into a new desktop so I won't get distracted. I love love love the Windows Task Switcher. Now I can just have Windows 365 as yet-another desktop.
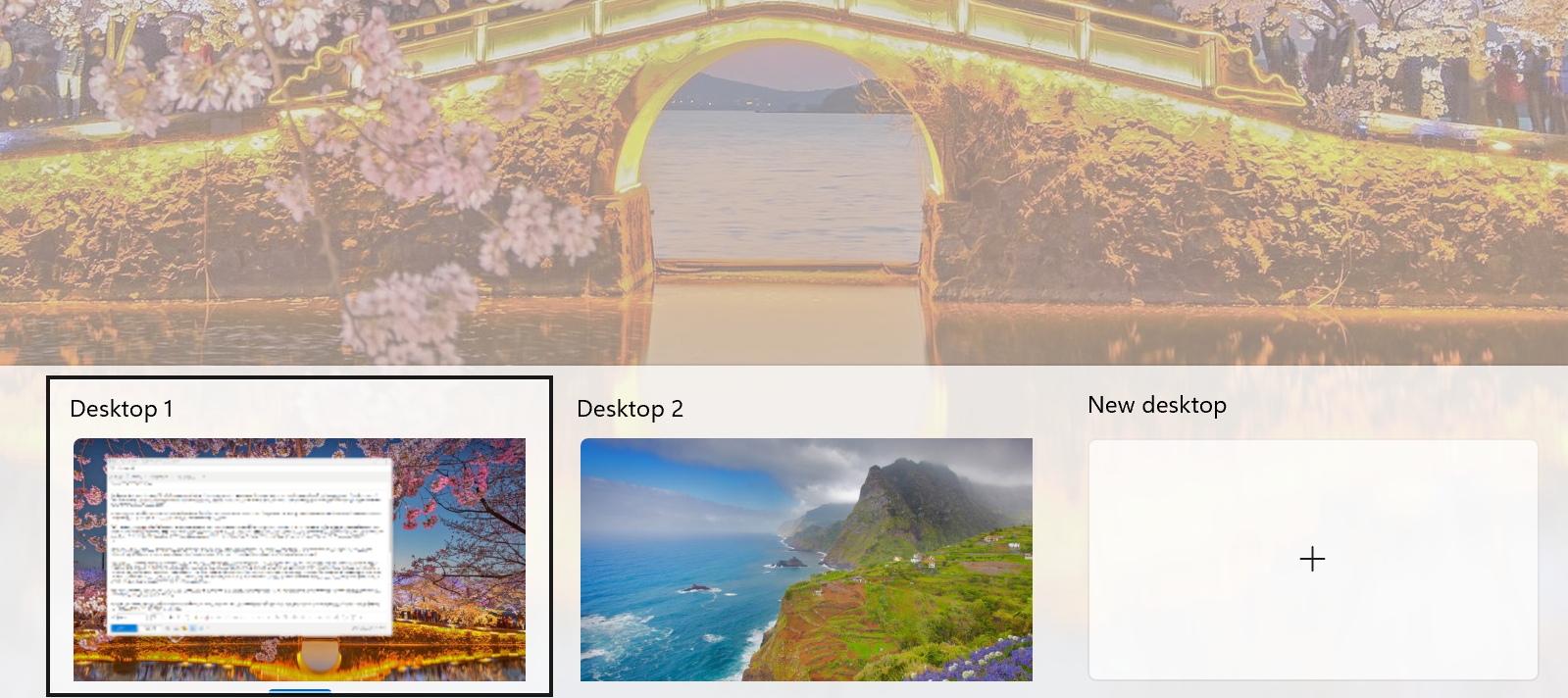
Boot to Windows 365 is another one that took me a moment to unravel. At first it looked like this was just a shined-up registry replacement of the Windows Shell, but this will allow the native local Windows authentication experience (CTRL+ALT+DEL) to use Windows Hello, authenticate directly to Azure AD, and deliver the user into their Windows 365 experience. To do that requires tools that aren't already present in Windows, so while it may ultimately be a shell redirection, it's redirecting something that isn't there yet today.
And its main purpose is to support frontline workers at multi-user devices. We've already seen how Windows 365 can run persistent sessions for less than the cost of optimized Azure Virtual Desktop's non-persistent sessions, so why not take those advantages and let users run walk-up sessions and remain confident that their processes don't break just because someone else needs the local device.
By far the biggest moon-shot announcement around Windows 365, however, was offline mode. This will allow users to work in Windows 365 even when Internet is unavailable, then resync all changes back to the cloud automatically when Internet access is restored. It sounds pretty amazing, and comes with a few caveats. The first is that it will evidently only support "certain workloads," and at this time we don't really know what that means, but the second pair of caveats comes from the Microsoft Mechanics Studio video that demonstrates a very alpha implementation. In it, Scott Manchester specifically states offline mode will be for "premium Windows endpoints." From that statement we can glean a couple of key details that allow me to speculate on exactly how this will be implemented, along with a couple of potential pitfalls.
First, obviously: Windows. We know Microsoft has been closing the feature-parity gap between MacOS and Windows client apps, but I think it's safe to say offline support will come to Windows first...and maybe Windows only. And that's because Apple (at least to my cursory recovering-Mac-user knowledge) doesn't have a first-party hypervisor. Windows can run Hyper-V or Sandbox natively with just a feature install.
But that brings us to the 2nd point: "premium Windows endpoints." Running Hyper-V comes with resource consumption, and with those 3 words I think they're basically saying this will effectively run the VM in both the local Hyper-V AND in the cloud with delta-shipping. That's an early speculation, but it means you'll need to run offline-mode Windows 365 instances on machines that have adequate resources to handle that load. Much like how only 8-vCPU W365 instances can run nested virtualization, I imagine offline mode will run a hardware check, and configuration of it will almost certainly require an elevation to install Windows features.
All of this seems really cool, but there's room for error. Admins will need to review the hardware specs very carefully before promising offline-mode support to users, and from my own experience, installing Hyper-V can have interesting ramifications for other apps in Windows, particularly those that use hardware acceleration.
From what I'm hearing, though, we have at least until early calendar-year 2023 to get all our testing sorted for this one.
Now, beyond the integrations between the local and cloud PC, we also got a bunch of announcements around management. We've known about native Azure AD Join for a while, and we've demoed it in previous webinars. We also got localization support and the ability to run our network endpoints natively within Microsoft's hosted networks, but we got a little more details about the point-in-time restore capability, which is now generally available. First of all: it's now generally available! Woohoo! But while you, the admin, can set granular control on how frequently which PC's are backed up, the service reserves 4 of your 10 backup slots for weekly backups.
Windows 11 got a big shot in the arm with a FASCINATING introduction by Satya, who called Windows 11 "the biggest update to our operating system in a decade." That's a forceful statement considering Windows 10 was introduced in 2015, and was at the time touted as "the last version of Windows." Windows 11 is being treated as a fundamental paradigm shift in end-user computing.
Smart App Control brings MDAC (Microsoft Defender App Control) power to small business by exposing cloud intelligence and treating local apps much like Microsoft Defender for Cloud Apps treats...well: cloud apps. If you haven't seen MDAC (now WDAC because why not?) in action, it's a policy-driven native instrument that extends the power of SmartScreen to blocking unsigned apps from running on a Windows device. This is a fantastic augmentation to traditional AV because AV relies on specific signatures and heuristic behaviors. If malicious code behaves in a way that's not expected to AV, it gets through. WDAC & Smart App Control allow you to shut that door, even for unsigned apps that are known to be safe.
Personal Data Encryption was also announced as an upcoming feature for Windows 11, and this one initially felt superfluous until I dug into it a little bit. So your PC is turned on and protected with BitLocker. You're at the OS and working fine, and you step away from the PC. The file system, though encrypted, is unlocked. Drive-by attackers can extract your files, whether by local screen access or, assuming you locked it, by some malicious local device access. Your data is no longer yours. With PDE, though, there's a secondary encryption tying your files to your Windows Hello passwordless credential. These files are NOT unlocked, even though the file system is. An attacker cannot replay your Windows Hello credentials to unlock the files. The user experience is much the same as what we've come to love about Microsoft Information Protection: a visible padlock on the file and no restrictions on sharing as usual.
If you've seen my demos on Windows Information Protection, you'll be familiar with the briefcase icon that accompanies data stored in and accessed from corporate locations, whether files or apps or even protected websites. Coming soon to Endpoint Manager will be the ability to take similar actions on personal devices with Edge profile policies. Configured identically to other app protection policies, these will allow us to force users on personal devices to establish a corporate-managed profile in Edge to access corporate data. No other management will be imposed, and the user can be restricted from sharing data from one browser session to another, or to any other app on the personal device. This remains one of the single biggest requests I hear year after year, and I'm really thrilled that we're getting lighter-touch ways to deliver these protections while enabling users to be productive on (largely) their own terms.
Windows Autopatch, which was introduced in preview at November's Ignite, will become generally available for Windows E3 (and E5) customers in July. Autopatch manages the updating of all core Microsoft components on a Windows endpoint, combining the OS, Office, and Edge update cycles into a single solution that is optimized for secure productivity. The service will support a ring-based deployment workflow, like what we've been using in Endpoint Manager for the past 18 months or so, but will also introduce auto-remediation capabilities in the event that something goes wrong. Autopatch will be added free to Windows E3 & above, and will be extended over time to include driver & firmware updates.
Remote Help became generally available, and we also got a new tab in the Tenant Admin section of Endpoint Manager for other Premium add-ons. These premium add-ons have additional licensing implications, and Microsoft explicitly stated that their plan is to support additional premium capabilities over time.
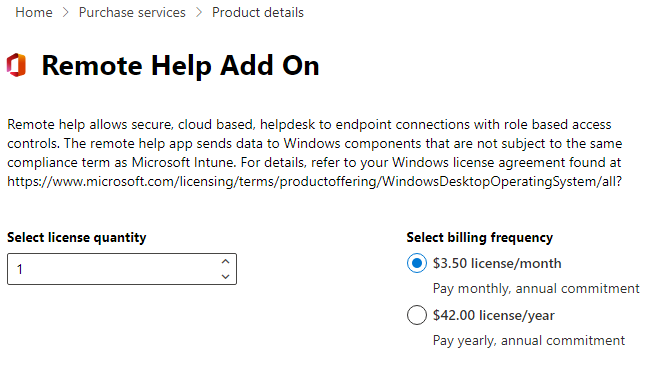
As the first generally-available item in that list, though, we finally got pricing for Remote Help, which is available per-user at $3.50/month or a flat cost of $42/year. A calculator will tell you those are the same, but it's actually a radio-button choice. Remote Help is the tool you'll need to bypass UAC elevation prompts in customer-support calls.
A screen-grab of the video shows additional add-ons that are not in my tenant, and reveal some of the other management capabilities that may appear as premium add-ons over time. What I'm really curious to know is if these will all be first party features, or if they'll open Endpoint Manager to 3rd party plug-ins like Defender for Endpoint briefly did with Cyren's web content filtering solution (before they just bought the product). What they did say, though, is that as these features fill out, they plan to offer a single consolidated step-up bundle for Microsoft 365 customers.
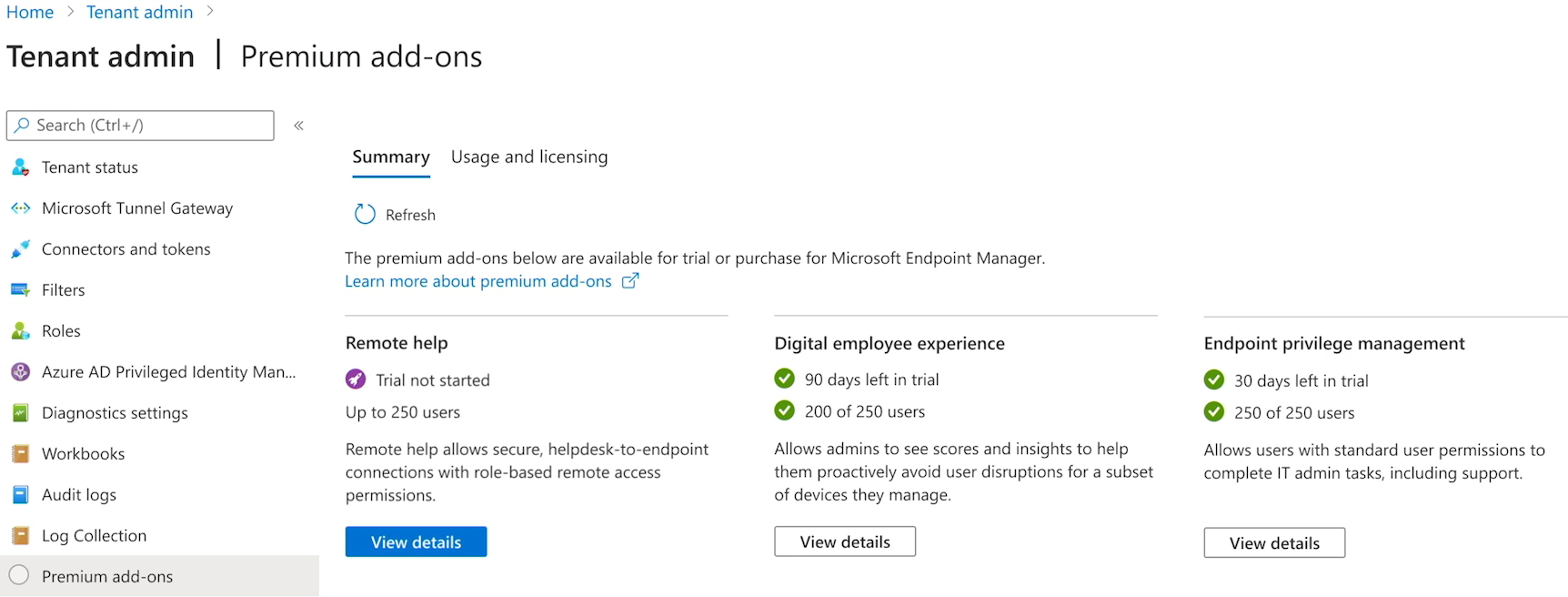
Endpoint Analytics will also transition from a reactive to a proactive stance with the new Endpoint Experience Management Capability, detecting crashes and changes in device performance to notify IT before the user experiences significant downtime. More details to come on that one.
Ok so that was a HUGE volume of content. I'm still trying to digest all of it!


Comments