Azure AD Access Reviews
I can always tell when it’s audit season. Maybe it’s the crunchy leaves or the shorter days or the smell of despair as admins put down important admin stuff to regurgitate the same tired reports they’ve produced every year for the past million years: what accounts have access to what? Why do they have that access? Do they still need it? Will this ever end? Why can’t they get this information themselves?
Can you tell it’s not my favorite part of the identity & access management lifecycle?
So I’ve felt the pain as I’ve heard murmurs from some of our customers in the past couple weeks. And I made lots of herbal tea and rolled up my sleeves and talked about Azure AD’s Identity Governance capabilities. A lot. I mean a lot a lot.
It’s no accident I chose it as the subject of one of our fall webinars.
I’ve talked both here and in our video content about how to align resources (groups, teams, SharePoint sites, apps) into catalogs and then publish access packages from those catalogs. I’ve even shown how we can define separation of duties such that specific access packages cannot be held by the same person at the same time. I’ve shown you how to manage requests, multi-stage approvals, automatic expiration of access and even what to do with guest accounts that have no standing access.
But while we’ve talked access reviews, too, I’m not sure they’ve gotten the center-stage treatment they deserve. Because I’m gonna guess audit season isn’t your favorite, either.
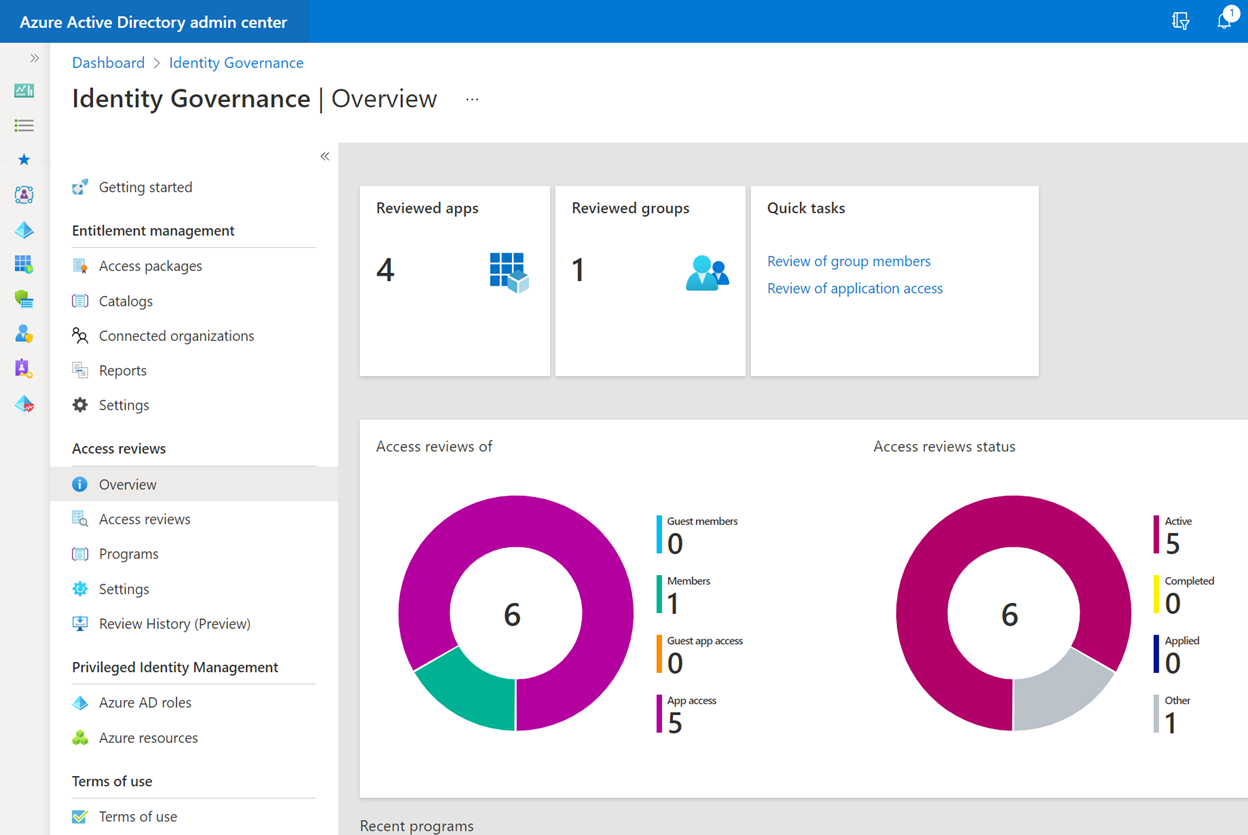
Access reviews are exactly what they sound like, except you’re passing the work to Azure AD to manage on your behalf.
We can monitor and review access for all sorts of stuff in Azure AD, though the interfaces aren’t fully aligned. We can monitor users & guests, their access to apps, roles, groups, sites, teams, and even Azure resources and roles.
We can specify who does the reviewing, too. Is it the users themselves? Their managers? Designated SME’s? If I’ve defined catalog owners and other role-holders in Identity Governance, I might consider having them either be the reviewer or the recipient of the final report.
We can define review durations and recurrence properties from just one time to annually.
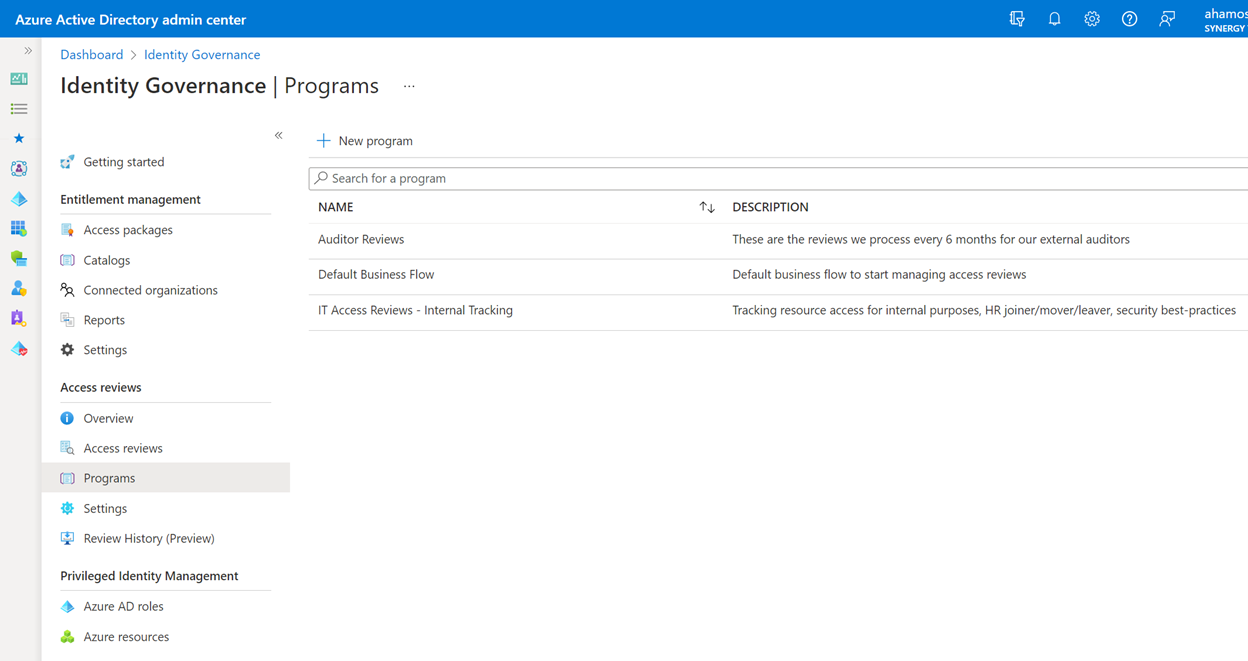
We can take these access reviews and group them logically by purpose in review programs, so we can keep track of what’s for the auditors and what we’re tracking for our own internal purposes:
We can define automatic actions to take upon completion, and actions to take if the audit request is ignored. No more chasing people to get their answers: if they don’t respond, they lose the access! And no more trying to interpret people’s justifications for why they need access: their own words are part of their official response to the request—if it doesn’t fly for the auditor, that’s not your problem any more! And at the end of the audit we can have the access review automatically send its results to anybody we want: internal or external.
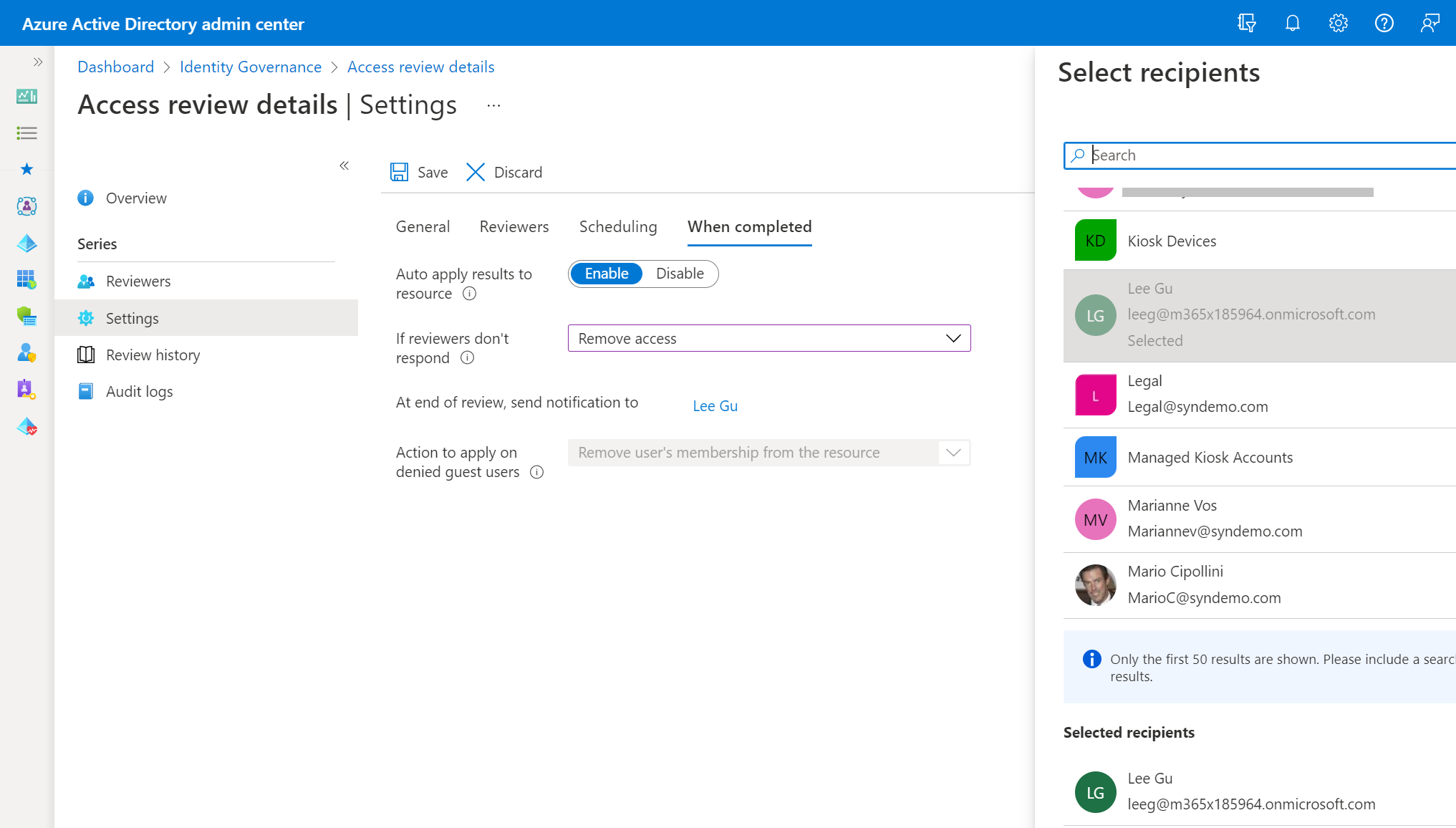
Go ahead and put your auditor’s contact info in your Azure AD. Why not: this is your party!
You can define multiple reviews for the same resource, too, but be careful you don’t create too many reviews that have the same people answering the same questions over and over, or they might stop answering and accidentally revoke their own access.
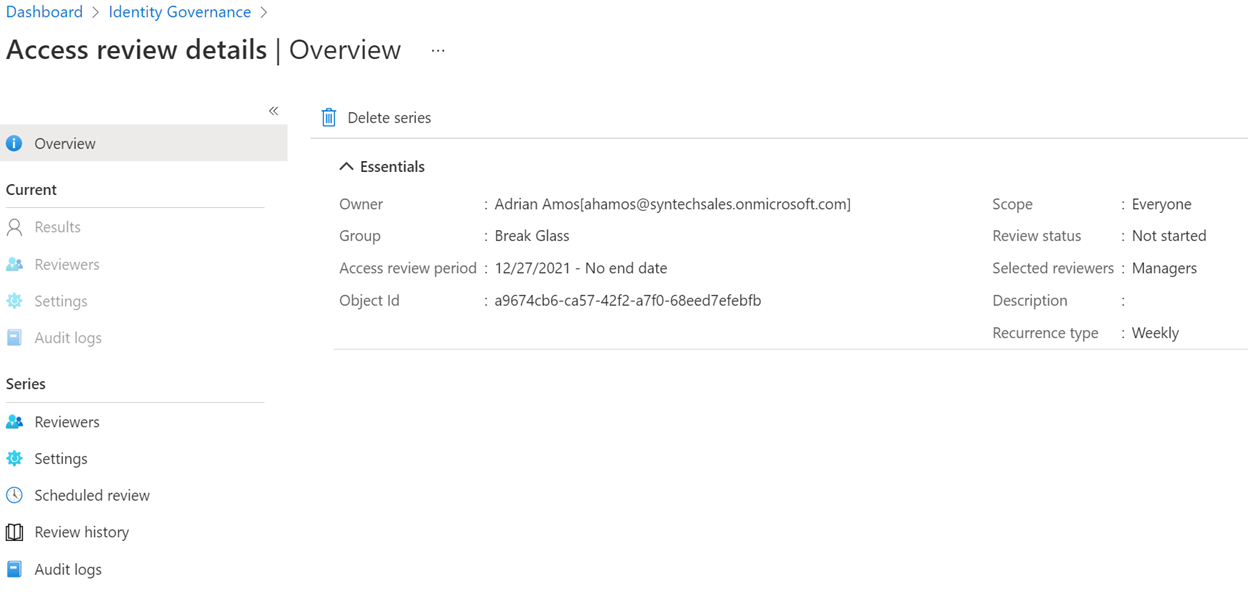
Using a ‘break glass’ group with an assigned Azure AD role to handle emergency admin elevation? It’s a great trick to ensure you can always get back in if a conditional access policy nukes the environment, Privileged Identity Management has no way to automatically revoke that access. Access Reviews can bridge that gap, though:
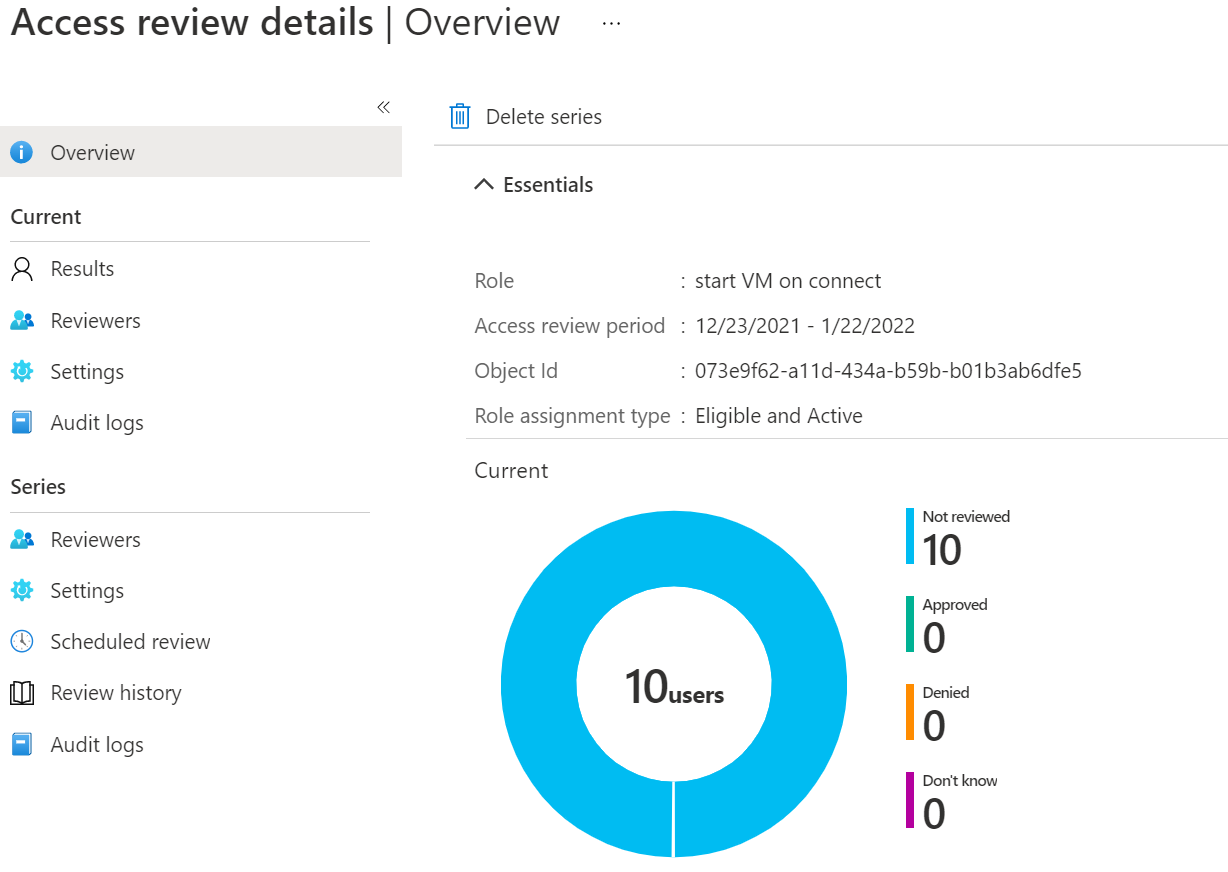
Using Azure Virtual Desktop for personal desktops and you’ve enabled some cost-cutting measures to park unused VM’s overnight? Make sure the right users have the custom Azure role to start VM’s on connect:
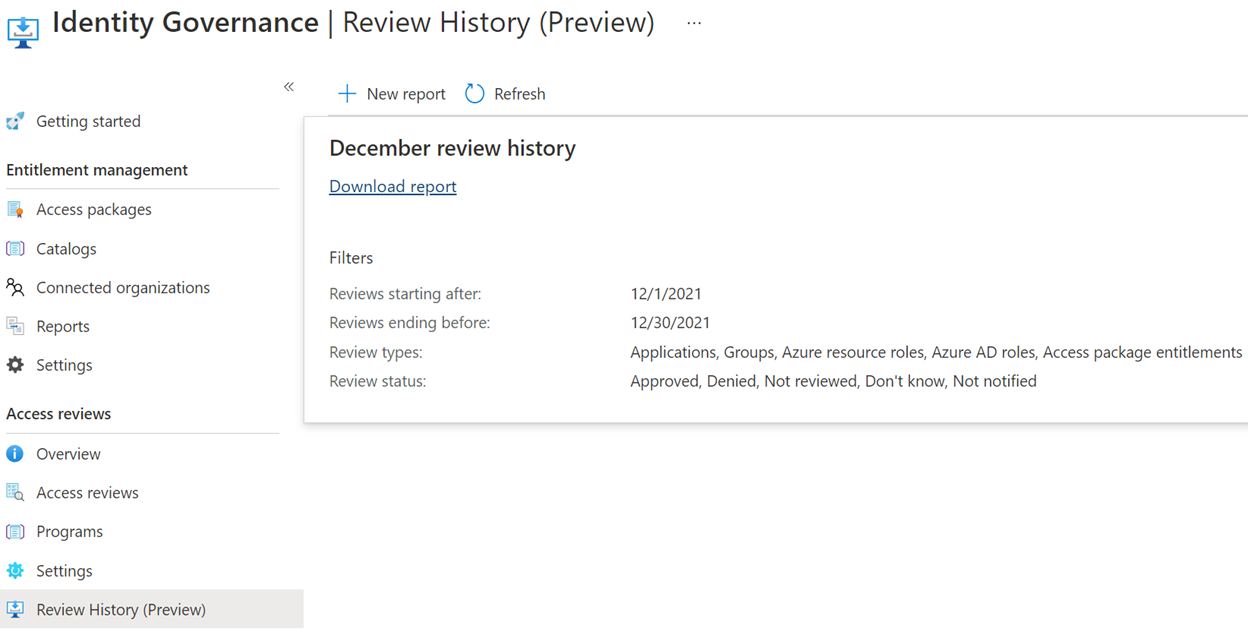
And of course you can audit all the auditing and report on all the reporting, but you can also run a review of all the reviews in the past 30 days with ‘Review History’:
If you're in your busy audit season, I hope this will help relieve at least some of the stress and pain associated with the tasks at hand.
Would you like to find out more about Azure Active Directory? Learn how you can deploy Azure Active Directory today.


Comments